AD/LDAP-Based Authentication to CDESK with Account Management
PAGE CONTENTS
Activating the AD/LDAP connector simplifies the user management in CDESK. By grouping AD accounts and setting attributes you can automate the creation and parameterization of accounts in CDESK. Subsequently, it solves the authentication of user access to CDESK.
The AD/LDAP connector verifies the validity of the Microsoft Active Directory or LDAP account at the time the user logs in to CDESK. The automatic creation of accounts in CDESK is based on the AD account membership in the selected groups. According to the attributes, accounts can be assigned to companies, and a user’s supervisor and job position can be specified for them.
Connecting CDESK and AD/LDAP through this connector results in users logging in using credentials from AD or LDAP databases. Depending on the settings, you will be able to choose whether to display the domain selection on the initial login screen or display the domain selection with a login in the form name@domain.
Adding an AD/LDAP Connector in CDESK
To add an AD/LDAP connector, go to Global Settings -> Connectors, API. When clicked, a list of added connectors is displayed. To add a new connector, click the +Add Connector button located in the upper right corner.
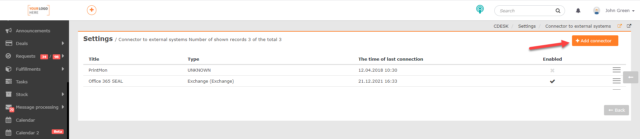
When clicked, a window for selecting the connector type is displayed. Select the AD/LDAP (Directory Service) option and then click ->Continue.
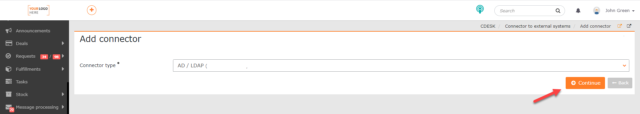
When clicked, a window for configuring the parameters is displayed. The window is divided into several tabs, which are described in the following paragraphs.
Preparation – Loading the AD Tree in Third-Party LDAP Software
To simplify the process, we recommend that you load the data from AD into the LDAP software. In the following procedure we will use Softera LDAP Browser, which can be downloaded on this link.
When successfully installed, add a new connection. To do this, click the New button located in the top bar.
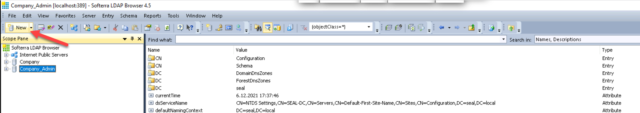
When clicked, a modal window will appear. First enter the name under which the structure will be displayed and then click Next.

Then insert the address and the port of the Active Directory server and click Next.

In the next step, the authentication method is selected. Select Other credential and enter a password in the Password field. Once the details entered, click Finish.

Basic AD/LDAP Connector Settings
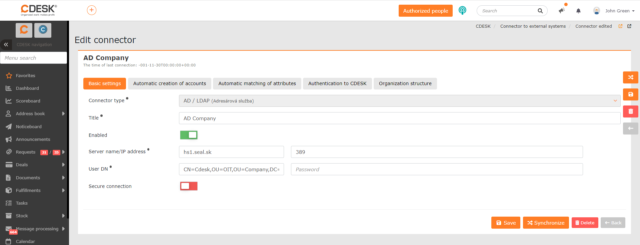
Connector type – field is not editable and is filled in automatically.
Title – the name under which the connector will appear in the list of connectors.
Enabled – connector can be used by placing the switch in the on position ![]() .
.
Server name/IP address – in the first field, enter the name or IP address of the server and in the second field, enter the port number. The default port for AD communication is TCP/UDP 389.
User DN – the user who will read data from the AD for CDESK. It is sufficient that he has read-only permissions to the necessary parts in the AD. The user can be specified in the form domain/user. It is also possible to use the path from AD. To get the path, look up the user in the LDAP software, right-click on it and select Properties. When clicked, a modal window will appear with the user’s parameters. The required path is located in the very first row on the Entry tab.

In the Password field, enter the password that the user uses in AD.
Secure Connection – if you have the option of a secure connection with the AD server, put the switch in the on position ![]() and change the port from 389 to 636.
and change the port from 389 to 636.
Automatic Creation of Accounts
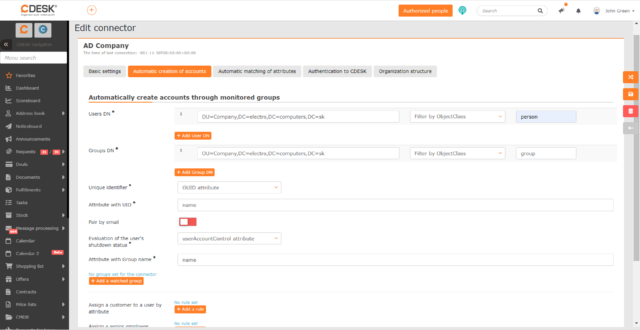
User DN path – the path where users are located to create and/or pair accounts in CDESK. Next to this field is a setting where you can set whether all records falling under the given path will be loaded, or only objects falling under a certain objectClass. ObjectClass represents the attribute according to which users are registered and sorted in the LDAP software. When you select Filter by ObjectClass, the objectClass selection box appears next to the User DN path field. The +Add User DN path button is used to add an additional path from which users will be loaded. For each new path, filtering by objectClass can be set.
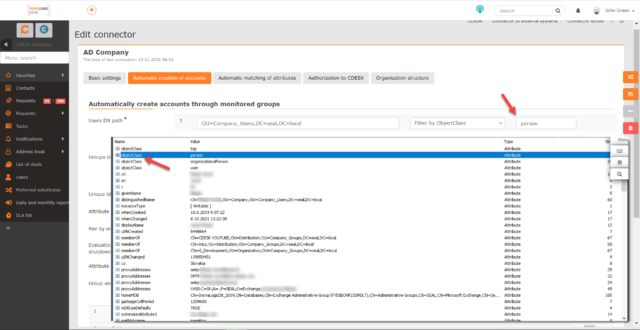
Group DN path – specifies the path to load the groups. This setting is important so that individual groups from LDAP are assigned the user groups used in CDESK. You can specify whether to load all records falling under the given path, or only objects falling under a specific objectClass. The +Add Group DN path button is used to add another path from which groups will be loaded. For each new path, filtering by objectClass can be set.
Unique identifier – means data that is read from LDAP into CDESK and based on this data the user is synchronized. This identifier remains the same even if the user’s login and other personal data is changed in the LDAP software.
If you are using Active Directory, we recommend that you leave the GUID Attribute option selected. After the accounts are successfully created, the GUID attribute will be transferred to the newly created user in the External ID entry on the General Settings tab of the CDESK account settings.
If the data in the LDAP software is loaded from another system, select Custom Attribute. When you select this option, the attribute entry box appears. We recommend using an attribute similar to the objectGUID attribute used in Active Directory. This is so that the user is uniquely identified throughout the lifetime of the AD account.
Attribute with UID – we recommend using the value sAMAccountName, however, if necessary, it is possible to insert another value with no spaces. When the account is created in CDESK, this value will pre-populate as the Username. (This value can be found on the General Settings tab under Users and Groups->Users-> choose a user.)
Pair by email – If the switch is on ![]() , new accounts will not be created for users who have the same email in CDESK as in Active Directory. If you leave the switch in the off position during synchronization
, new accounts will not be created for users who have the same email in CDESK as in Active Directory. If you leave the switch in the off position during synchronization ![]() , duplicate accounts will also be created for users already registered. Turning the switch back on during the next synchronization will not remove the duplicate accounts. Therefore, we recommend that you enable this switch during the first synchronization.
, duplicate accounts will also be created for users already registered. Turning the switch back on during the next synchronization will not remove the duplicate accounts. Therefore, we recommend that you enable this switch during the first synchronization.
Evaluation of user’s shutdown status – is the attribute based on which the user status (active/inactive) is evaluated. In AD, the userAccountControl attribute is used for this by default. Therefore, if you are not using custom settings, select this option. No other settings are made when this option is selected, because CDESK automatically recognizes the code for active and inactive users. If you are using a custom parameter to evaluate user status, select Custom Attribute. In this case, a field will appear to enter the attribute that will be used to evaluate the status.
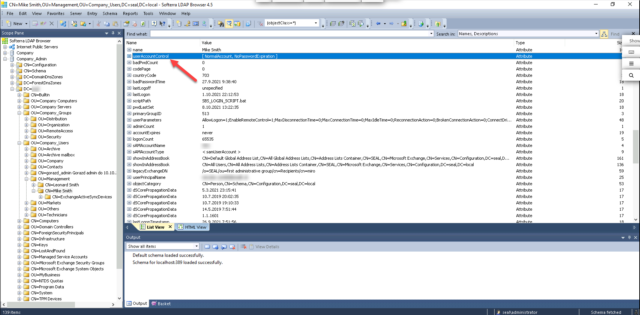
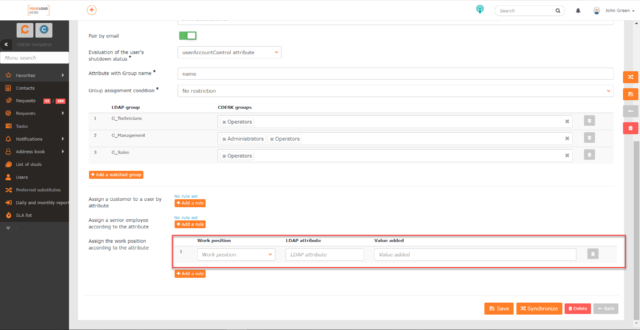
Attribute with group name – specify the attribute that will be used to display the group name. It is recommended to choose the name value or sAMAccountName. This name will also be displayed below in the Group Assignment Condition section.
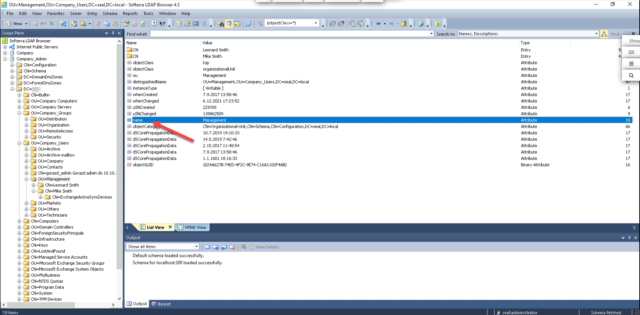
Group Assignment Condition – this setting is displayed only after the connector is saved. To save the settings, click on the Save icon located on the bar on the right as well as at the end of the form. After saving the settings, you need to synchronize with the LDAP software. This is done by clicking the Synchronize icon, which is located on the bar on the right as well as at the end of the form.
After successful synchronization, this section will display the groups belonging to the path specified in the Group DN Path field and a field next to each of them for setting the user group in CDESK. Only user accounts belonging to LDAP groups that appear in this list are created in CDESK. Any user group registered in CDESK can be selected for an LDAP group, and multiple CDESK groups can be assigned to a single LDAP group. In this case, users will be given the permissions associated with all selected CDESK groups.
For the Group Assignment Condition setting, you can select the options No restriction and Only when user is created.
- No restriction – when this option is selected, the selected groups will be synchronized with each AD/LDAP connector synchronization. For example, a user belonging to a particular group in LDAP is in the Operators group in CDESK: he will be removed from this CDESK group. The next time the AD/LDAP connector is synchronized, it will again be automatically assigned to the Operators group because users from that LDAP group are assigned to the Operators group. If another CDESK group is set up for that LDAP group, the next time the user is synchronized, he will be assigned to that group with the proper CDESK permissions as well.
- Only when user is created – when this option is selected, the user will only be assigned to the CDESK group when at its creation and the group assignment will no longer be updated.
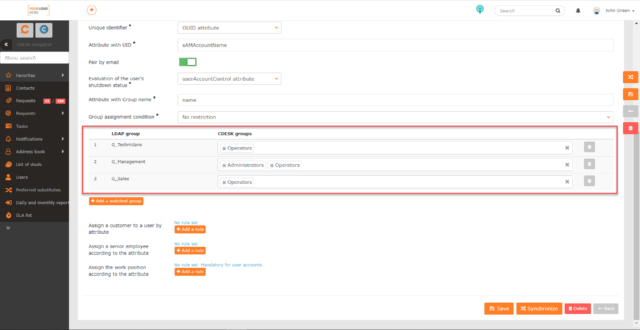
You can add another LDAP group to the list of groups displayed by using the +Add Watched Group button. When clicked, a list of available groups is displayed. Clicking the group name and then clicking the Add button will add the LDAP group to the list of groups to which CDESK groups can be assigned. You can remove a group from the list by using ![]() located at the end of each row.
located at the end of each row.
If you do not register groups in the LDAP software, or if you want to add all users regardless of group assignment, select No Group Designation after clicking the +Add Watched Group button.
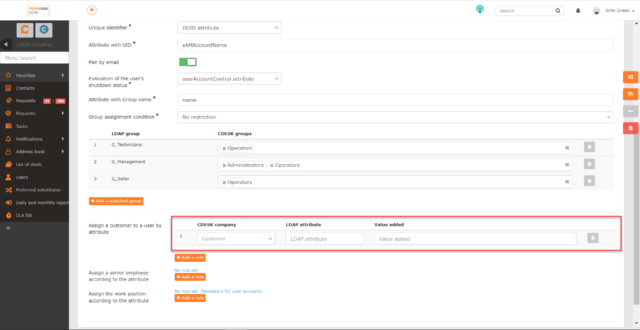
Assign customer to user by attribute – use this setting if you want to automatically assign a customer to newly created users in CDESK. This will allow users to enter requests, for example. When you click the +Add Rule button, a row with the following fields is displayed:
- CDESK company – when clicked, a selection with a list of companies registered in CDESK will be displayed. Select the customer that will be assigned to the selected users. The list of companies registered in CDESK can be found in Address Book -> Companies.
- LDAP attribute – an arbitrary attribute in the LDAP software that CDESK will use to evaluate whether the selected company will be assigned to users. If you want to assign a company to all newly created users and the users in question do not share any LDAP attribute, we recommend that you insert the value userAccountControl.
- Acquired value – the value of the selected LDAP attribute that, if met, will automatically assign the set company to users with the value. When selecting the LDAP attribute userAccountControl, it is recommended to use the value 66048 and/or 512. These are standard values in AD. 66048 indicates users whose password does not expire and 512 indicates users whose password expires.
To assign a company based on two or more LDAP attribute values, a new rule must be defined for each value. You can define it using the +Add Rule button. In this way, you can also define the assignment of users to another company in CDESK based on any LDAP attribute and its values. If you need to delete a rule, click ![]() at the end of the row for that rule.
at the end of the row for that rule.
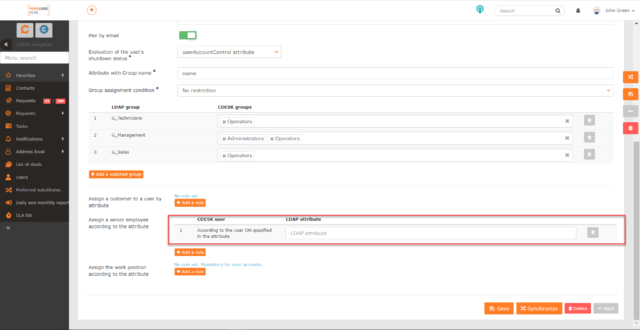
Assign senior employee by attribute – use this setting if you want to automatically assign a senior user to newly created users in CDESK. For example, it could be a company manager. When you click +Add Rule, a field appears to enter an LDAP attribute that, if met by the user(s) in the LDAP software, will assign them as senior employees to the newly created accounts. This can be any attribute. You can also add multiple rules to add a senior employee. If you need to remove a rule, click ![]() at the end of the row for that rule.
at the end of the row for that rule.
You can find the list of senior users for a specific account in Users and groups -> Users -> Users -> choose a user -> Supervisors and subordinates tab -> Supervisors section.
Assign job position by attribute – use this setting if you want to automatically assign job positions to newly created users in CDESK. When you click the +Add Rule button, a row with the following fields appears:
- Job position – click to view a selection of job positions registered with CDESK. Job positions can be created in Global Settings -> Job Positions -> Defining Job Positions.
- LDAP attribute – an arbitrary attribute in the LDAP software that CDESK will use to evaluate whether users are assigned to the selected job. If you want to assign a job to all newly created users and the users do not share any LDAP attribute, we recommend that you insert the value userAccountControl.
- Acquired value – the value of the selected LDAP attribute that, if met, will automatically assign the set job to users with the value. When selecting the LDAP attribute userAccountControl, it is recommended to use the value 66048 and/or 512. These are standard values in AD. 66048 indicates users whose password does not expire and 512 indicates users whose password do expire.
In order to assign a job based on two or more LDAP attribute values, a new rule must be defined for each value. You can define this using the +Add Rule button. In this way, you can also define the assignment of users to a different job position in CDESK based on any LDAP attribute and its values. If you need to delete a rule, click ![]() at the end of the row for that rule.
at the end of the row for that rule.
Automatic Matching of Attributes
The settings on this tab will only become available after the connector has been saved. The tab allows you to define rules for auto-filling additional user parameters.
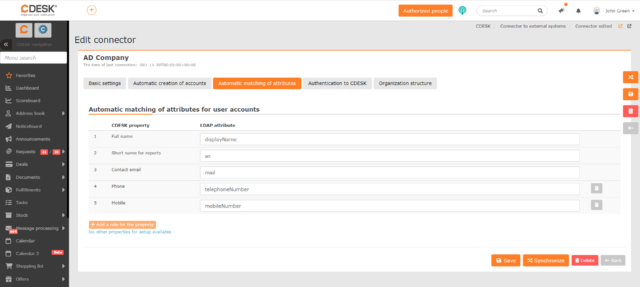
By default, the list contains properties that are mandatory.
Full Name – specify the LDAP attribute that populates the Full Name field in the user form. You can enter any attribute. However, we recommend using the displayName attribute.
Short name for reports – specify the LDAP attribute to populate the Short Name for Reports field in the user form. For CDESK, it is recommended that the Short Name for Reports be the same as the user’s login. Any attribute can be entered, however, we recommend using the sAMAccountName attribute
Contact email – enter the LDAP attribute that will be used to populate the Contact Email field in the user’s form. Any attribute can be entered. However, we recommend using the mail attribute.
If necessary, you can set the Phone and Mobile fields to pre-populate automatically. If you have other additional properties set up for users in your CDESK environment, it will be possible to add those as well. However, these must be global properties set for all users, which you can add in Global Settings -> Users -> Additional Properties section.
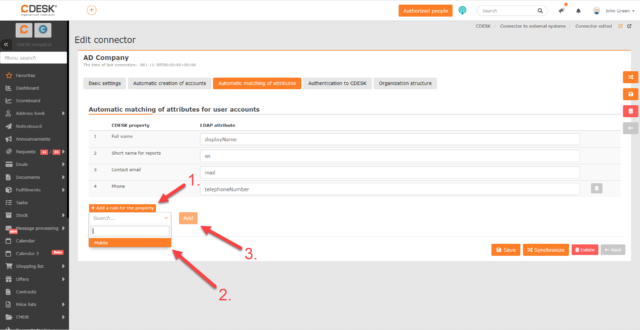
To add one of these properties, click the +Add Rule for Property button below the current list of properties.
When clicked, the property selection box will appear. Select the desired property and then click Add. The property is then added to the list and the box for specifying the corresponding LDAP attribute is displayed next to it. To remove a property added in this way from the list, click ![]() , located at the end of the property line. You can only remove attributes that are not required.
, located at the end of the property line. You can only remove attributes that are not required.
Authentication to CDESK
The tab allows you to set how newly created users will be authenticated when logging into CDESK. For more information on setting up CDESK login, see Setting the Way of Logging In to CDESK below.
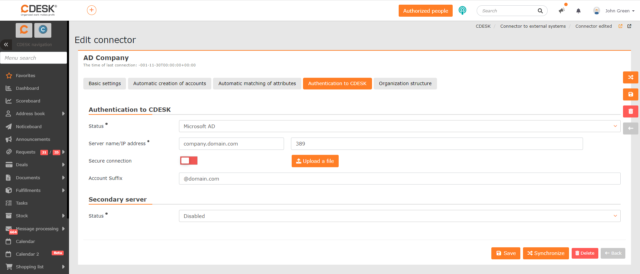
Status – the selection provides the following options:
- Disabled – default option. In this case the fields for other settings are not displayed. Use the Disabled status if you register multiple domains in the AD connector, which will result in the login data of newly created users containing multiple domains.
- Microsoft AD – use if you register all users in AD under one domain. When you select this option, additional fields for setting up the server for this domain will become available.
Server name/IP address – in the first field, enter the name or IP address of the server and in the second field, enter the port number.
Secure Connection – to make the connection secure, turn the switch on ![]() and upload the certificate using the Upload File button if necessary.
and upload the certificate using the Upload File button if necessary.
Account Suffix – the domain name in the form @domain.domain. This name will be selectable on the CDESK login screen if you have set up a manual method of connector selection.
Secondary server – if you are using multiple AD servers, this section allows you to configure login through a secondary server that will be used if the primary server fails. By default, the status field is set to Disabled. To set up the secondary server, select Microsoft AD and configure the data in the displayed fields in the same way as for the primary server, but with the data of the secondary server.
Transfer of Organizational Structure from Company to CDESK
On the Organizational Structure tab, you can configure the server data from which the company’s organizational structure is retrieved. According to the classification of the account in the organizational structure, it is possible to filter the records in the lists and include them in exports.
Once users are created, this organizational structure will be graphically represented on the Organizational Structure tab of the user’s form. (Groups and Users -> Users -> choose a user -> Organizational Structure tab). The path with the inclusion of a specific user in the organizational structure is also displayed in the list of requests, fulfillments and work orders.
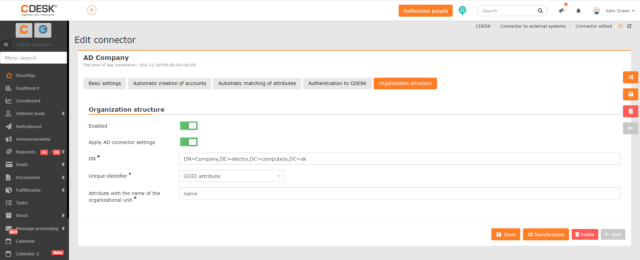
Enabled – the switch is in the off position by default ![]() . Place the switch in the on position
. Place the switch in the on position ![]() in case your company’s organizational structure is registered on a different server than the one you specified on the Basic settings. Setting the switch on will open the fields for setting the server parameters. Entering the parameters is the same as on the Basic settings.
in case your company’s organizational structure is registered on a different server than the one you specified on the Basic settings. Setting the switch on will open the fields for setting the server parameters. Entering the parameters is the same as on the Basic settings.
Setting the Way of Logging In to CDESK
Users with automatically created accounts can log in to CDESK in two ways. Either by using AD credentials or by using CDESK credentials.
The login method can be configured in Global Settings -> Logos, Domain, Files -> under How to select the AD Connector.
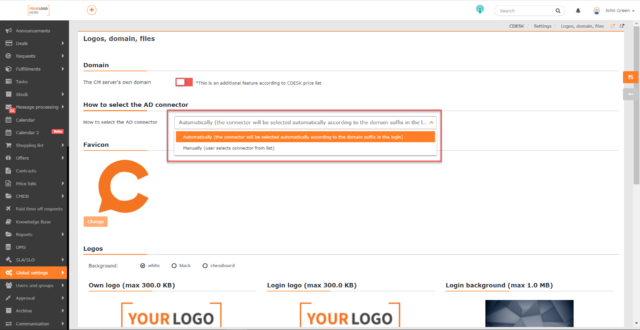
The selection offers the following options:
Automatic – use if you register multiple domains (account suffixes) in AD. In this case, the user will log in with a login in the form: user@domain.local. The connector will be selected automatically according to the domain suffix in the login name, so there will be no need to select the AD connector type when logging in.
- Manual – use if you selected Microsoft AD status when setting up the AD/LDAP connector on the Authentication to CDESK tab. In this case, the user selects the connector type when logging in.
To save your settings, use Save located at the end of the form and on the sidebar of the window.